Privacy Awareness Card
Privacy Awareness Cards are used in workshops for recognizing, analyzing, and reflecting on privacy risks encountered in everyday life.
The Privacy Awareness Cards have been specifically developed for use in workshops, where they are most effective as part of collaborative group work. They support participants in recognizing, analyzing, and reflecting on privacy risks encountered in everyday life. The card set and accompanying materials foster exchange and discussion in a hands-on learning environment. The Privacy Awareness Cards are intended as an interactive educational tool, primarily for groups participating in seminars, training sessions, and workshops.
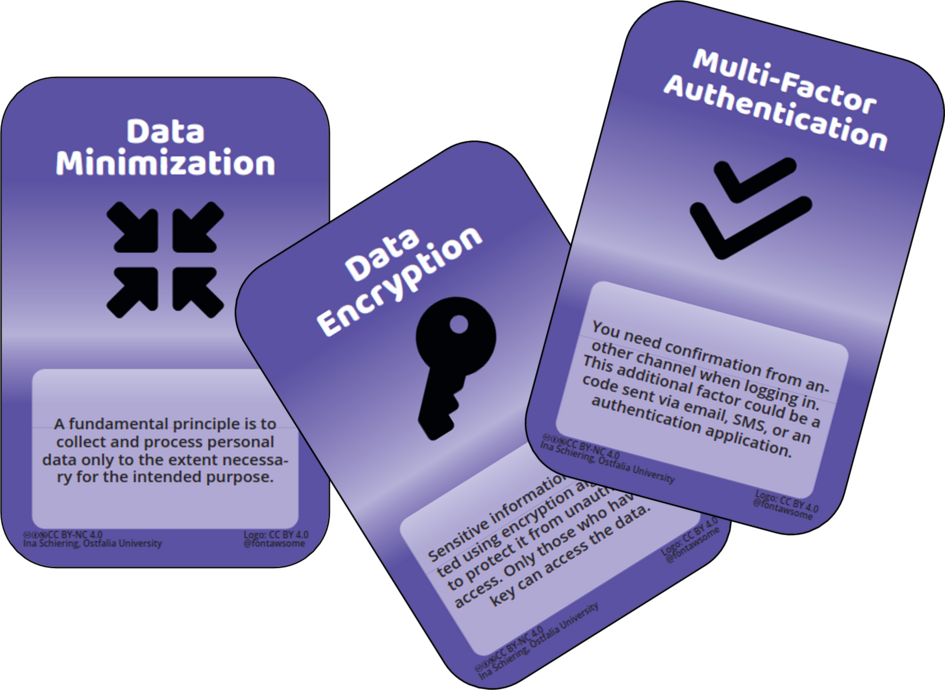
Participants can collaboratively analyze scenarios from their everyday lives in which potential data protection risks may occur. To support the analysis of these scenarios, Privacy Awareness Cards are used, which present typical examples of stakeholders within the scenarios, personal data, and impacts on affected individuals. Afterwards, privacy protection goal objectives can be used to document priorities and identify countermeasures.
The Privacy Awareness Cards include the following cards for scenario analysis:
- Scenario Cards: Which situation is being examined?
- Stakeholders: Who is involved?
- Data: What personal data about the individuals are being processed?
- Consequences: What are potential consequences for the individuals?
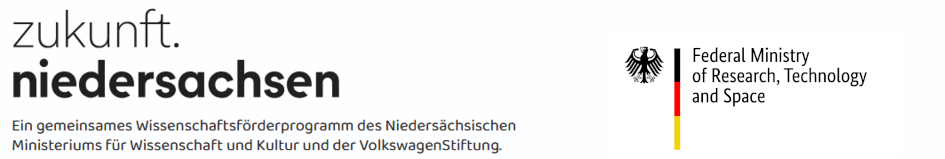
- Privacy Protection Goals: What are the priorities of the affected individuals based on the privacy protection goals confidentiality, integrity, availability, transparency, interveneability, unlinkability, and data minimization?
- Actions: What actions can the individuals take?
With these cards, participants can discuss and analyze within a workshop relevant scenarios from their everyday lives in groups. This workshop approach offers an accessible introduction to everyday privacy risks and empowers participants by giving them practical options for addressing those risks.
Structure of the Workshop
Objective:
Identify, understand, and prevent data protection incidents, or mitigate their consequences, within a participatory workshop.
Materials:
- Card Deck (Stakeholder, Data, Consequences, Actions, Privacy Protection Goals) incl. blank cards
- Board
- Scenario card with pen
- Rulebook
Procedure
1. Choose a scenario
Together, consider a scenario involving a data protection incident from your everyday life or work environment. Then, write down all relevant details on the corresponding scenario card. The more specific and precise your description of the incident, the easier it will be to complete the steps that follow.
Collaboratively develop a concrete scenario for a data protection incident. Think of an incident that could realistically occur in your everyday life, at school, during your studies, or in your workplace – or perhaps one that has already happened.
Describe the incident as precisely as possible:
- Where and when does it take place?
- How does the incident unfold?
- Who is involved?
- Which data is affected?
- How was the incident discovered?
Record all relevant details of your scenario on the scenario card. The more vivid and specific your description of the data protection incident is, the easier it will be to identify suitable stakeholders, data, consequences, goals, and actions in the next steps.
Can’t think of your own scenario? Get inspired by common data protection incidents: a lost USB stick, a misaddressed email containing sensitive data, unencrypted cloud storage, or accidentally sharing photos in a messenger group are classic examples. Remember: the more realistic the scenario, the more engaging the discussion!
Example:
On May 31, 2024, a significant data breach occurred at an international service provider for the online sale of tickets to concerts, sporting events, and other events. The personal data of approximately 560 million customers was exposed through a data leak. Among the information affected were names, addresses, phone numbers, and email addresses of users. Sensitive details about order history, including ticket purchases, also fell into the wrong hands. In addition, parts of payment data—including the cardholder’s name, the last four digits of the credit card, and the expiration date—were made public.
2. Select and Place Stakeholder, Data, and Consequences
Once you have described your scenario, go through the following three categories together and select the appropriate cards. Place the selected cards clearly visible on the board so that you have a clear overview of the data protection incident and the elements involved.
a) Stakeholder: Select the relevant stakeholders and place their cards on the board.
Consider which individuals, groups, or organizations are involved in or affected by the data protection incident. These might include, for example, employees, customers, supervisors, service providers, IT departments, or authorities. For each identified stakeholder, take the corresponding card and place it on the board.
If an important stakeholder is missing, use a blank card and label it accordingly.
Example:
In the context of the ticket sales data protection incident, several key stakeholders can be identified. As the affected person, I am at the center because my personal data has been compromised. The provider is responsible for protecting this data, while administrators are in charge of the technical security of the systems. Partner organizations, such as event organizers, may also be impacted, for example through loss of trust or cancellations. Additionally, legislators play an important by setting the legal framework for data protection and monitoring compliance with relevant regulations. In this specific example, we focus on the stakeholders "Self" and "Friends and Contacts."

b) Affected Data: Select the types of compromised data and place their cards on the board.
Next, analyze which specific types of data are involved in this incident. Are they address data, health data, login information, account details, or other types of personal information? Keep in mind that some data types can reveal even more— for example, location data can expose movement patterns, or timestamps can give insights into personal habits. Find the cards that represent the relevant data types and place them on the board.
Again, if you have a specific data type that isn’t included in the provided cards, use a blank card and label it accordingly.
Example:
In the case of the ticket sales data protection incident, the following types of personal data are particularly affected: financial information, as parts of payment data such as names, credit card details, and expiration dates were exposed. Order history and ticket details also provide insights into the hobbies and preferences of the individuals involved—for example, whether someone regularly attends musicals, sporting events, or specific artists or types of events. Address data can furthermore reveal details about a person’s housing situation, such as which district or city they live in.

c) Consequences: Select relevant consequences and place their cards on the board.
Now discuss together which direct and indirect consequences may result from the incident—such as financial loss, reputational damage, legal consequences, or loss of trust. Select all consequences that you think fit your scenario and place the corresponding cards on the board.
If an important consequence is missing, use a blank card to add it individually.
Example:
In connection with the ticket sales data breach, various consequences may arise for those affected. The disclosure of sensitive information (exposure) puts them at risk that personal details may be spread uncontrollably and misused by unauthorized parties. This can lead to so-called "chilling effects," meaning that individuals restrict their activities—such as purchasing tickets for certain events—out of fear of further data breaches or being observed. In addition, defamation can occur, for example if it becomes known which types of events, such as musicals or sporting events, were attended and this is viewed negatively in one's social environment.

3. Prioritize Privacy Protection Goals
Select the three most important Privacy Protection Goals for this incident and place them on the board in order of priority.
After you have placed all the cards for stakeholders, affected data, and possible impacts on the board, take another close look at your scenario. As a team, consider which data protection goals are most important in your specific case.
Go through the five classic data protection goals (confidentiality, integrity, availability, transparency, and intervenability). Discuss as a team which three goals should have the highest priority in your specific data privacy incident. For example, ask yourselves:
- Is it more important that unauthorized persons do not gain access to the data (confidentiality)?
- Or is it a priority that the data is always correct and accessible (integrity and availability)?
- Do transparency and the ability of data subjects to have a say play a special?
Agree on the three most important goals for your scenario. Place the corresponding data protection goal cards on the board in the order of your priorities—first the most important, then the second and third most important.
Briefly justify your selection so everyone understands the reasons for your chosen order.
There is no absolute "right" or "wrong" in this process—the key is to have an open discussion and thoughtfully consider the key aspects of your scenario as a team.
Here are the Privacy Protection Goals:
- Confidentiality Personal data may only be accessed or processed by authorized individuals. Unauthorized persons must not have access. The goal is to protect information from unauthorized access, disclosure, or publication.
- Integrity The accuracy and completeness of personal data must be ensured. Data must not be altered, deleted, or falsified unintentionally or without authorization. This ensures that stored information remains correct and reliable.
- Availability Personal data must always be available and accessible to authorized users when needed. System failures, data loss, or accidental deletions must not result in data becoming lost or inaccessible.
- Transparency The processing of personal data should be understandable and traceable for the individuals concerned. They must be able to know when, how, and why their data is used. This also includes being informed about their rights.
- Intervenability Data subjects must have the ability to influence how their data is processed, for example through requests for information, corrections, blocking, or deletion of their data. Errors or misunderstandings in data processing should also be easily correctable.
- Unlinkability Separate data records must not be linked in such a way that individuals can be identified or their behavior can be extensively monitored. The goal is to prevent the creation of detailed personal profiles or comprehensive surveillance through the combination of different pieces of information.
Example:
Confidentiality is especially important to me as a user, because I want to ensure that personal information such as my name, address, and payment details do not fall into the wrong hands and get misused. Transparency is also crucial: I want to understand which data is collected when I purchase tickets, how it is used, and whether it is shared with third parties. Only with this knowledge can I give my informed consent to using the service.

4. Determine Actions
Discuss together which concrete actions could help prevent such an incident in the future. Place suitable measure cards on the board.
Now, take a close look at your scenario on the board, with the chosen stakeholders, data types, impacts, and your prioritized privacy protection goals. Together, consider which concrete measures could help to prevent a similar data privacy incident in the future or at least mitigate its consequences.
Discuss different approaches as a group:
- Which technical, organizational, or personnel-related measures could help?
- Are there also non-technical solutions that make sense?
Talk about why you are choosing certain measures and how they can help to improve data protection. Make sure that your selection matches your previously prioritized privacy protection goals and is as practical as possible.
It’s perfectly fine if you’re not very familiar with data protection measures—this is exactly why there are many measure cards included in the deck. You can simply look through the cards to get an overview.
However, make sure not to select measures at random. The goal is to identify appropriate and meaningful measures for your specific scenario. For each card, consider whether it really fits the situation and how it could help.
Example:
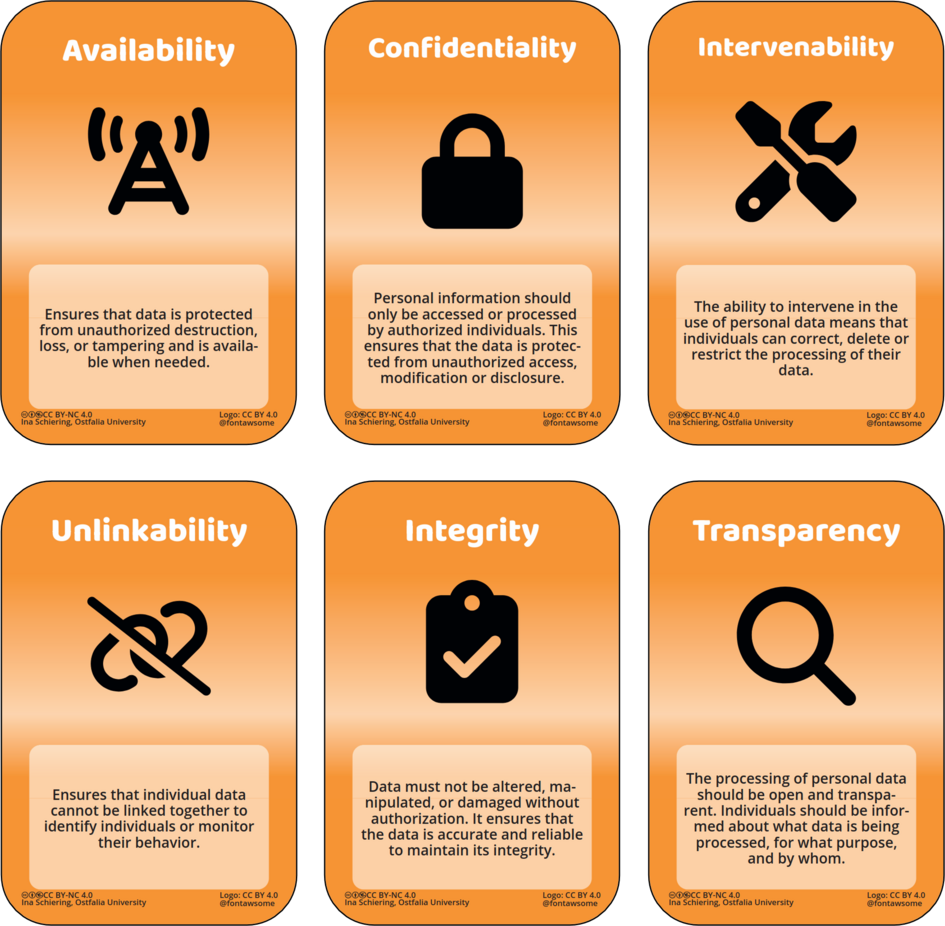
In connection with the ticket sales data breach, three measures are particularly relevant: data minimization, data encryption, and multi-factor authentication. Data minimization means that only those personal data are collected which are truly necessary for purchasing a ticket. For example, one might ask whether a full address is really required for an online ticket, or whether providing just an email address would be sufficient for ticket delivery. The same applies to payment information—careful consideration should always be given to how little data actually needs to be stored or displayed. As a customer, I also have the option to critically review online forms myself, considering whether I really need to provide all the requested data or whether I can limit myself to only the required information.
In addition, data encryption is essential to ensure that sensitive information such as payment details is protected from unauthorized access—both during transmission and while stored. Finally, multi-factor authentication can significantly enhance the security of internal systems for operators. If a secure two-factor authentication process had been implemented in this case, the incident might have been prevented or at least contained. Together, these measures reduce the risk of data theft and make handling sensitive data much safer overall.
5. Discussion and Reflection
Discuss alternatives, possible improvements, and your personal views regarding priorities and measures.
After placing the cards on the board, take some time to discuss your results as a team. This step is especially important to reinforce what you have learned and to include different perspectives.
Together, review your scenario, the involved stakeholders, the types of data affected, the selected impacts, your prioritized privacy protection goals, and the measures you have chosen. As you do so, discuss the following questions:
- Which decisions were easy, and which were difficult to make?
- Are there any alternative solutions or measures that you might have overlooked?
- With what you know now, would you prioritize or select any measures differently?
- How effective and realistic do you think the chosen measures are in your everyday life or work environment?
- What challenges might you encounter when trying to implement them?
Personal reflections:
- What aspects of privacy protection do you consider most important?
- Did this workshop make you aware of any risks or problems you hadn’t considered before?
- Were there any surprises or new insights?
Feedback and suggestions for improvement:
- What did you particularly like about the workshop, and what could be improved for next time?
- What topics or scenarios would you like to explore in the future?
The workshop is finished once you have fully developed and discussed your scenario as a team. You have now gained an overview of the risks, identified the most important privacy protection goals, and selected appropriate safeguards—congratulations on successfully completing the workshop!
Tip: Be creative! The goal is to develop an understanding of privacy risks and possible solutions.
Example:
After analyzing the ticket sales incident, it became clear which types of personal data could be affected in such a data breach—for example, name, address, parts of credit card information, and ticket preferences. The analysis also highlighted that such an incident can impact not only individuals themselves but also their social circles. For instance, private preferences or activities may be unintentionally disclosed, or a person’s reputation may be damaged.
Additionally, concrete protective measures were identified: When buying tickets online, it is advisable to carefully consider which information is truly required and to be as sparing as possible with your personal data. It is also essential that service providers implement effective security safeguards such as data encryption and multi-factor authentication.
This analysis provided practical insight into how mindful and responsible handling of personal data should look in our digital daily lives.
Publications, Copyright and Contact
Publications
Lorenz, T., Pleger, M., Böhm, T., & Schiering, I. (2024), Privacy Awareness Cards-A Serious Game for Privacy Awareness. In: Friedewald, M. & Karaboga, M. (Eds.): Freedom in digital infrastructures. Poster-Proceedings. Research Papers of the Platform Privacy, No. 4., 13-16 Karlsruhe: Fraunhofer ISI, 2024. https://doi.org/10.24406/publica-3685 (external link, opens in a new window)
Copyright:
2025 – CC BY-NC 4.0 - Ina Schiering, Ostfalia University of Applied Sciences
Contact:
- Tom Lorenz, Faculty of Computer Science
- Michael Pleger, Faculty of Computer Science
- Prof. Dr. Ina Schiering, Faculty of Computer Science
Sponsored by: